
Before partnering with Integrity Technology Solutions, many organizations find themselves navigating uncertainty. They’re unsure of their true risk exposure, questioning whether their current provider is delivering on promises, and lacking clarity around the effectiveness of their security controls. They’re asking, “What’s next for us?” while struggling with slow response times, unreliable systems, and fragmented communication. Integrity steps in to eliminate that ambiguity.
We provide proactive insight, responsive support, and strategic alignment that ensures every technology investment drives value, not waste. From business continuity, cybersecurity strategy and support, to augmenting internal IT resources, we deliver confidence, clarity, and control so our clients can move forward with purpose.
Co-managed IT support is a collaborative approach where an external IT provider works alongside your internal IT team to enhance capabilities, fill gaps, and provide strategic guidance. It’s not about replacing your staff. It’s about empowering them with additional resources, specialized expertise, and scalable support to ensure your technology runs smoothly, securely, and efficiently.

Integrity Technology Solutions delivers comprehensive IT cybersecurity and support services designed to protect, empower, and evolve as your business needs change. From day-to-day helpdesk support to strategic CTO/CIO-level consulting, we tailor solutions that align with your risk tolerance, internal resources, and regulatory requirements. Our services include proactive threat detection, incident response, data protection, and compliance-driven security planning, ensuring your systems are secure, your team is supported, and your business is ready for what’s next.

Integrity Technology Solutions offers both fully managed and co-managed IT services designed to meet organizations where they are, whether they need a complete outsourced IT department or expert reinforcement for their internal team. Our fully managed services provide end-to-end support, from infrastructure and cybersecurity to compliance and strategic planning, allowing businesses to focus on growth while we handle the tech. For larger organizations, our co-managed model delivers seamless collaboration, filling gaps in expertise, capacity, or coverage with responsive support and deep industry knowledge. In both models, clients benefit from proactive monitoring, clear communication, and a security-first approach rooted in the NIST Cybersecurity Framework.

Integrity Technology Solutions provides expert-level professional services and consulting services that help organizations plan, implement, and optimize critical IT initiatives. From designing secure, scalable network infrastructure and cloud environments to deploying advanced security controls and AI-driven solutions, our project resources bring deep technical expertise and industry insight. We support digital transformation through SharePoint and Microsoft 365 application consulting, enabling collaboration, automation, and governance. Our team also conducts comprehensive risk assessments and facilitates Tabletop exercises to strengthen incident response readiness and align with NIST CSF. Whether leading full-scale implementations or augmenting internal teams, we deliver strategic guidance and hands-on execution that drive measurable outcomes.

Partnering with the industry’s top providers to ensure compliance, security, and performance.







Discover the leadership and certified experts trusted to keep your business secure and compliant.

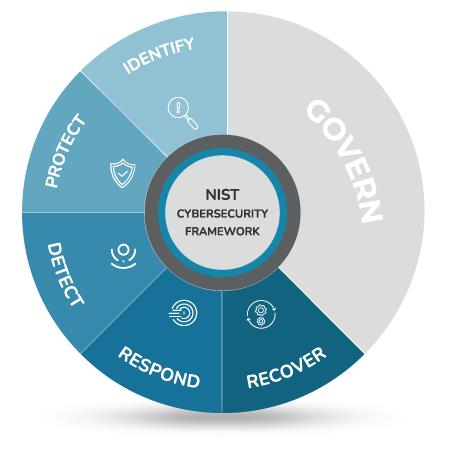
Integrity Technology Solutions uses the NIST Cybersecurity Framework to keep your business secure, resilient, and ready for what’s next.

Whether you’re in IT or leading the business, we’re built to support you.
Contact us today to start a conversation.
At Integrity Technology Solutions, we make switching IT providers simple and stress-free. Our team supports organizations of all sizes to ensure every step—from onboarding to ongoing support—feels smooth, transparent, and built around your goals.
“Switching to Integrity is one of the best business decisions that I’ve made.”
— Ulises Napoles
Vice President, First Site, Ltd.
